Quantum-safe cryptography
What is quantum-safe security?
We live in a world governed by the laws of quantum mechanics. Quantum computing is a paradigm shift in computer science and engineering that involves harnessing the laws of quantum physics to build a fundamentally different kind of computer that is able to efficiently solve many types of problems that are intractable on the computers (and even supercomputers) in the world today. Some of the problems that quantum computers efficiently solve include factoring large numbers and the discrete logarithm problem. These are the same mathematical problems upon which almost all of today’s widely deployed public key cryptosystems are based – including RSA and most forms of Elliptic Curve Cryptography. Therefore, these systems would be easily broken by an adversary with access to a quantum computer. Quantum algorithms also require key length increases for symmetric-key algorithms such as AES, but fortunately the damages to symmetric key systems – in contrast to public key systems – do not require entirely new cryptographic algorithms.
As a result, as quantum computers scale to larger numbers of quantum bits (“qubits”), the time required for breaking these cryptosystems rapidly approaches zero. Quantum-safe cryptography and security refers to research efforts to identify cryptographic primitives that are resistant to attacks from both classical and quantum computers, as well as to modify existing security protocols (such as SSH, SSL/TLS, S/MIME, IKE, and others) to accommodate these changes in primitives. The end goal of these efforts is to find cryptographic algorithms that aren’t vulnerable to cryptanalytic attack by conventional or quantum computers, allowing security of information assets to be maintained into the post-quantum world.
| Algorithm | Key Length | Security level (conventional computer) |
Security level (quantum computer) |
|---|---|---|---|
| RSA-1024 | 1024 bits | 80 bits | 0 bits |
| RSA-2048 | 2048 bits | 112 bits | 0 bits |
| ECC-256 | 256 bits | 128 bits | 0 bits |
| ECC-384 | 384 bits | 256 bits | 0 bits |
| AES-128 | 128 bits | 128 bits | 64 bits |
| AES-256 | 256 bits | 256 bits | 128 bits |
Why does it matter to government and industry?
Without quantum-safe cryptography and security, almost everything that ever has been – or will be – sent over a network is vulnerable to attack. Even messages encrypted using an unbroken cryptosystem sent before the advent of a large-scale quantum computer could be stored in a data center, only to be later decrypted once the necessary quantum computational resources become available.
Since industries have legal and ethical obligations to the protection of consumer data, as well as a vested interest in keeping internal data secure, quantum-safe security needs to be a part of a company’s technology roadmap. For the information security industry in particular, making calculated investments against a high-risk/high-impact technological advance such as quantum computation is essential in toward building customer trust in the security of vendor products in the years to come.
While the publicly-known current state-of-the-art quantum computers are not yet at the scale to mount devastating attacks against our public key cryptosystems, the advances needed for scalable quantum computing may come very rapidly – and depending upon the adversary, may not even be made public knowledge until it is too late. As a consequence, any industry where the confidentiality or authenticity of information has value must take seriously the threat of quantum computers in their near-term cybersecurity threat assessment and risk management practices.
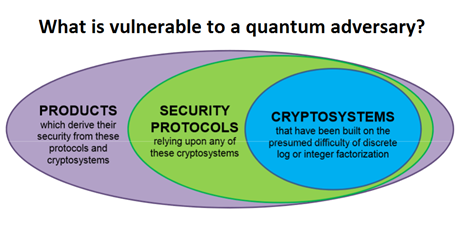
Toward quantum-safe cryptography and security standards
In an effort to make the transition to quantum-safe security possible for government and industry, researchers within the Institute for Quantum Computing and CryptoWorks21 are currently working with a global network of industrial, government, and academic partners to develop standards for the deployment of cryptography and security protocols across the network stack that are secure against quantum adversaries. In creating standards for security products, the world will be able to confidently deploy well-tested cryptographic primitives and protocols that will interoperate seamlessly within our existing security architecture, and to secure the world’s information assets against quantum attacks.
Individuals and organizations interested in being a part of the standardization process can learn more about the ETSI Industry Specification Group in Quantum-Safe Cryptography here.
